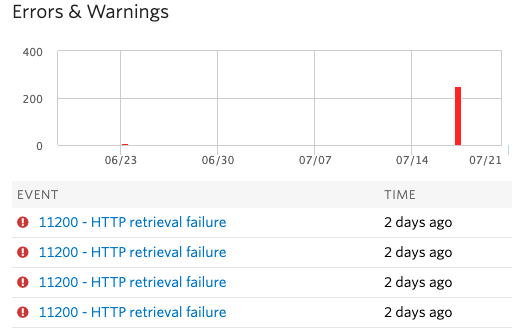
linkTimeline
Thursday, Jul 18 2019
4:00 PM - Attack begins to slowly ramp up
6:39 PM - First Twilio email, blocking Serbia prefix +381604427
7:20 PM - Start of large spike in call volume
7:21 PM - Attacker switches to only using UK phone numbers (+44)
7:25 PM - Responded to Twilio to request account suspension
7:30 PM - Our anti-abuse system kicks in, starts blocking excessive phone verification endpoint requests
7:31 PM - Disabled funding on Twilio
7:31 PM - We blocked IPs associated with requests
7:47 PM - Twilio responds that account is suspended
linkThe attack
Attack started around 6 PM, with most expensive calls being those that were disconnected at 7:30 PM (remaining connected for long periods of time). These ended after billing was turned off, resulting in ~ $-1600 account balance. These were not ended by Twilio, despite being similar Serbia (+389) prefixes to what they blocked at 6:39 PM
Switched to +44 (UK) numbers once Twilio started banning Serbia, etc prefixes.
Total number of attempted calls: ~1,090
busy: 30
canceled: 2
completed: 554
failed: 400
no answer: 104
linkRandom tidbits
Twilio customer for ~8 years
Typical bill has grown from ~$30/month to a peak of ~$200/month for all services (Voice, SMS, and Lookup).
Integration of voice verification pre-dates Twilio's "risky countries" geographic permissions segmentation.
We've slowly enabled additional geographic permissions over time, as our customers have contacted support.
Attacker used UK numbers - not exactly a "risky country" which could be omitted from Voice verification
linkCall volume and charges
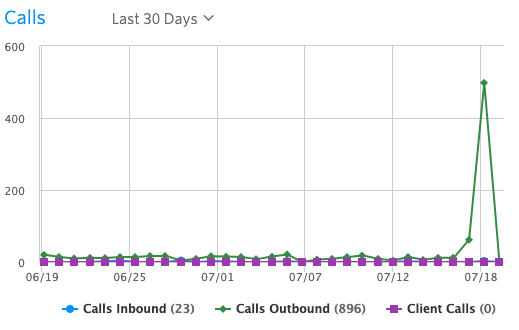
~550 calls, to the tune of ~$4500

Typical monthly bill around $50 for voice, ~10 calls (outbound) per day:

Our rate limiting blocked 249 calls, probably would have been another $2000-$2500: